
Leuchter CMDB - geprüfte Lösung mit Superagent
Die Leuchter CMDB (Configuration Management Database) ist, wie der Name vermuten lässt, eine Eigenentwicklung. In...
Since Windows 8, Windows Defender is pre-installed on every device. In addition, with the product Security Essentials, Microsoft offers a solution working also on older Windows operating systems.
Until Windows 10 and Windows Server 2016, for a company’s seamless and consistent protection, the product system Center Endpoint Protection has been offered. It was based on the well-known patterns of Windows Defender and Security Essentials but allowed a central administration. Since Windows 10 and Windows Server 2016, these products have been standardised under the name Windows Defender. Centralised management requires a System Center Configuration Manager infrastructure.

The cloud service Microsoft Defender for Endpoint can also be obtained directly from Microsoft. However, the configuration and deployment should be well thought out. For companies that do not have the know-how in-house, we offer the service additionally with configuration services, distribution and other services, completely adapted to the needs of your industry. We also advise companies on all aspects of using the service.
We offer interested parties a telephone exchange to answer questions. Please leave your contact details here!
The basis of a threat analysis consists of a baseline of selected security KPIs. These measuring points specifically query the security-relevant settings that are considered important for a company. Anomalies such as malware attacks, vulnerabilities in software, PUAs (unwanted software) or insufficient patch levels are detected and reported in real time. Uniform querying across the entire client environment provides a consistent statement about the security and health status of your client landscape.
For an attacker to successfully cause damage to your IT infrastructure, two things are necessary:
1. an existing vulnerability and
2. a way to exploit it.
While most malware protection systems detect when malware attempts to infect a system via a vulnerability, MS Defender for Endpoint Service starts one step earlier in the infection chain: Based on an extensive thank bank maintained by specialists, MS Defender for Endpoint Service detects vulnerabilities in the operating system as well as in deployed (third-party) software. This provides the opportunity to intervene before an attack on your IT infrastructure occurs.
MS Defender for Endpoint Service detects conspicuous behavior that often occurs when malware exploits vulnerabilities. These actions are detected at the file, storage, and network levels, recorded, and sent to the cloud for analysis. This gives you the ability to evaluate noticeable behavior. In the event that an attack has occurred, you simultaneously have evidence for further investigation for damage mitigation and forensic prosecution.
The software inventory used on a client is directly related to the vulnerability of the end device. Insufficiently up-to-date software or unwanted programs offer attackers the opportunity to damage your IT infrastructure or cause data leakage due to security vulnerabilities. This can cause lasting damage to your business. A well thought-out authorization structure can help to avoid unwanted software installations. Nevertheless, in practice, it has been shown that consistent control of the software inventory is a major challenge, which grows as the period of use of a client progresses. MS Defender fr Endpoint Service is available for controlling and managing the software inventory across your entire client landscape. You get the possibility to get a holistic overview of the deployed software at a central point and to start granular detailed queries if necessary to be able to intervene immediately.
Finding and exploiting vulnerabilities through malware used to be the business of an interested hobby. Today, finding, exploiting, reporting, and closing security vulnerabilities represents an institutionalized activity of an entire industry with well-established processes. When security vulnerabilities are found, software vendors are usually given a short period of time to close them before they are publicly disclosed. Ordered patch cycles then usually roll out the improvements automatically to the end devices. This approach ensures that all parties have a vested interest in ensuring software security, but at the same time increases transparency in finding attack surfaces. In practice, it is often the case that clients do not receive the latest security updates due to malfunction or misconfiguration, which represents an eminent risk, especially for endpoints with Internet/mail access. MS Defender for Endpoint Service collects information across the entire client infrastructure and reports outages centrally and immediately. This gives you the opportunity to react accordingly in terms of security.
The increasing complexity caused by technical progress places increasingly higher demands on the understanding of the assessment of IT security incidents. This demands financial and time resources from the operator of an IT infrastructure and distances him from the core business including his economic service provision. In order to be able to respond to potential threats as quickly as possible and at the same time relieve you of non-value-adding tasks, the specialists at Leuchter IT Infrastructure Solutions AG take over the initial measures, assess the security incident for you and discuss the next steps with you.
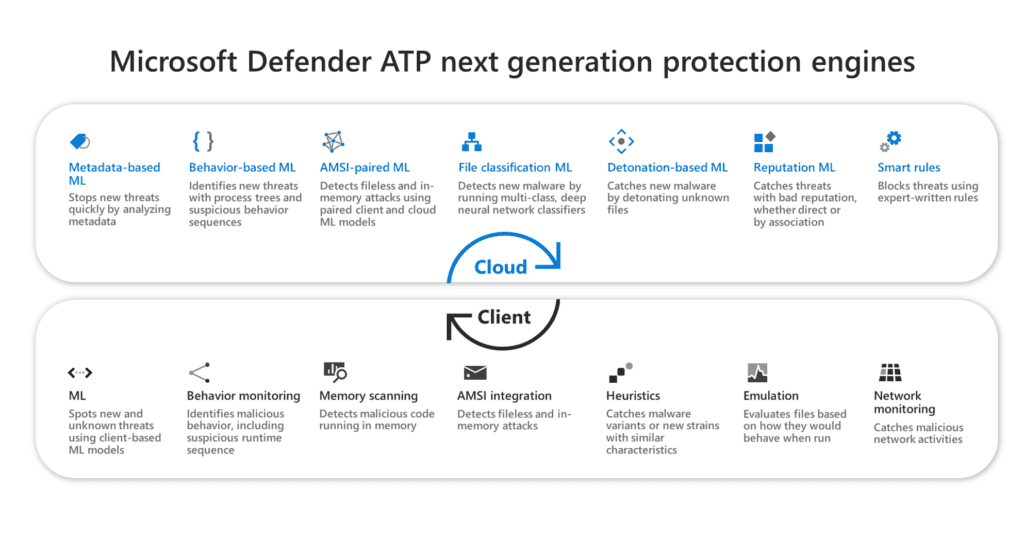
Microsoft collects billions of telemetry data worldwide every day. This unique repository of data is referred to by Microsoft as the "Microsoft Intelligent Security Graph." Through the application of machine learning, artificial intelligence and big data analytics, this data is processed to identify specific patterns of behavior that could indicate malicious activity such as malware or another type of attack. The insights from the "Microsoft Intelligent Security Graph" flow into Microsoft Security products such as Microsoft Defender for Endpoint in real time and deliver unparalleled protection.

Die Leuchter CMDB (Configuration Management Database) ist, wie der Name vermuten lässt, eine Eigenentwicklung. In...

In einer Zeit geopolitischer Unsicherheiten und wirtschaftlicher Herausforderungen fragen sich immer mehr Unternehmen...

Cyberangriffe nehmen weltweit zu – und machen auch vor der Schweiz nicht halt. Besonders gefährlich wird es, wenn...
A team of various professionals will take care of your inquiries concerning the topics IT infrastructure, organisation, communication and co-operation in the modern business world. Please consign your questions and messages to our team. A proven expert in these topics will contact you.
We look forward to your inquiry!